My First Security Project
Azure Honeynet and SOC Project: Cyber Attacks in Real Time
Introduction
In this project, I simulate a small-scale honeynet that attracts real-world traffic from attackers around the world through Microsoft Azure. The goal throughout this project is to demonstrate best security practices, incident response tactics, and the effects of hardening your environment. We’ll accomplish this by intentionally deploying virtual machines that have no protection from the public internet to attract attackers into our environment. Then, after ingesting some log sources into the Log Analytics Workspace, Microsoft Sentinel will come in to create attack maps, alerts, and incidents. In order to showcase metrics before and after hardening the environment based on the incidents generated from the 24-hour capture.
Azure Components Utilized
- Azure Virtual Network (VNet)
- Azure Network Security Group (NSG)
- Azure Virtual Machines
- Log Analytics Workspace with Kusto Query Language (KQL) Queries
- Microsoft Defender for Cloud
- Azure Blob Storage Accounts
- Azure Sentinel
Architecture Before Hardening
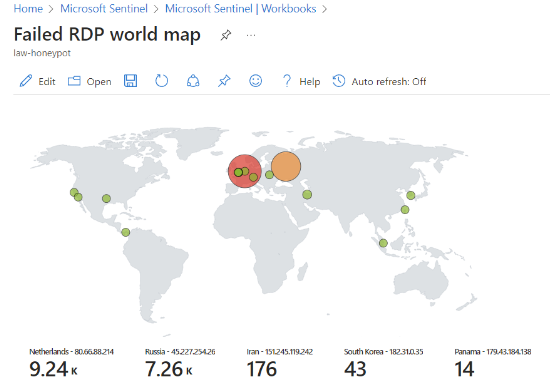
- In the “BEFORE” stage of the project, all resources were initially deployed with the hope that attraction would be gained from the public internet. The Virtual Machine had both their Network Security Groups (NSGs) and built-in firewalls wide open, allowing unrestricted access from any source. Additionally, all other resources, such as storage accounts and databases, were deployed with public endpoints visible to the internet, without utilizing any Private Endpoints for added security. These machines were then left to the public for 24 hours to generate the following attack maps mentioned earler.
This attack map showcases the number of incidents generated by leaving the Network Security Group (NSG) open.
Thi s attack map showcases the number of incidents generated by leaving the Network Security Group (NSG) open after some more additional time.
This attack map showcases the number of incidents generated by leaving the Network Security Group (NSG) open after a full 48 hours.
Powershell and KQL
To extract the data from the virtual machine of the log in attempts a powershell script was used. The image below shows a sample response from the script when a login attempt was executed.
The following screenshot is of the KQL code in the Azure Log Analytis Workspace to present the data from the power shell script of a global map. This is usually an after though in the Cybersecurity, actually presenting the results and showing data why this business sector is critical.
After Hardening Measures and Security Controls
In the “AFTER” stage, based off the incidents created from the “Before” 24 hour capture, I implemented hardening measures and security controls to improve the environment’s security from attackers.
These improvements included:
Network Security Groups (NSGs): I hardened the NSGs by only allowing my own public IP address to come through otherwise all other traffic would be blocked by the new parameteres created.
Built-in Firewalls: In my virtual machines I configured the built-in firewalls so that it would deny access from unauthorized users.
Attack Maps After Hardening / Security Controls
All map queries actually returned no results due to no instances of malicious activity for the 24 hour period after hardening.
Utilizing NIST 800.61r2 Computer Incident Handling Guide
For each simulated attack I practiced incident responses following NIST SP 800-61 r2.
Each organization will have policies related to an incident response that should be followed. This event is just a walkthrough for possible actions to take in the detection of malware on a workstation.
Preparation
- The Azure lab was set up to ingest all of the logs into Log Analytics Workspace, Sentinel and Defender were configured, and alert rules were put in place.
Detection & Analysis
- Assigned alert to an owner, set the severity to “High”, and the status to “Active”
- Identified the primary user account of the system and all systems affected.
- A full scan of the system was conducted using up-to-date antivirus software to identify the malware.
- Verified the authenticity of the alert as a “True Positive”.
- Sent notifications to appropriate personnel as required by the organization’s communication policies.
Containment, Eradication & Recovery
- The infected system and any additional systems infected by the malware were quarantined.
- If the malware was unable to be removed or the system sustained damage, the system would have been shut down and disconnected from the network.
- Depending on organizational policies the affected systems could be restored known clean state, such as a system image or a clean installation of the operating system and applications. Or an up-to-date anti-virus solution could be used to clean the systems.
Post-Incident Activity
- In this simulated case, an employee had downloaded a game that contained malware.
- All information was gathered and analyzed to determine the root cause, extent of damage, and effectiveness of the response.
- Report disseminated to all stakeholders.
- Corrective actions are implemented to remediate the root cause.
- And a lessons-learned review of the incident was conducted.
Conclusion
In this project, a mini honeynet was constructed in Microsoft Azure, and log sources were integrated into a Log Analytics workspace. Microsoft Sentinel was employed to trigger alerts and create incidents based on the ingested logs. Additionally, metrics were measured in the insecure environment before security controls were applied and then again after implementing security measures. The significant reduction in security events and incidents following the implementation of security controls highlights their effectiveness in safeguarding the environment.
It is worth noting that if the resources within the network were heavily utilized by regular users, it is likely that more security events and alerts may have been generated within the 24-hour period following the implementation of the security controls.