Creating a File Integrity Monitor
Where security meets transparency.
In the realm of digital security, the concept of integrity holds significant weight. Ensuring the integrity of shared files is paramount to maintaining trust and reliability.
Especially now when anyone can create malicious code with an AI model it is imperative to have an extra layer of security for sensitive files, data, applications and devices by routinely scanning and monitoring.
By upholding the integrity of the files, users can trust that the information they access is accurate and reliable.
The Goal
When data is mentioned it is usually in three forms:
- Data At-Rest
- Data In-Transit
- Data In-Use
My file integrity monitor specifically applies to data at-rest, which is where attackers often attempt to modify files and compromise their integrity. By focusing on data at rest, the FIM ensures that files stored on servers or databases remain unaltered unless authorized.
A file integrity monitor adds an essential layer of security, defending stored data against unauthorized modifications. Detecting a threat early in the cyber kill chain gives the organization a better chance to prevent data breaches before any data exfiltration occurs.
How it Works
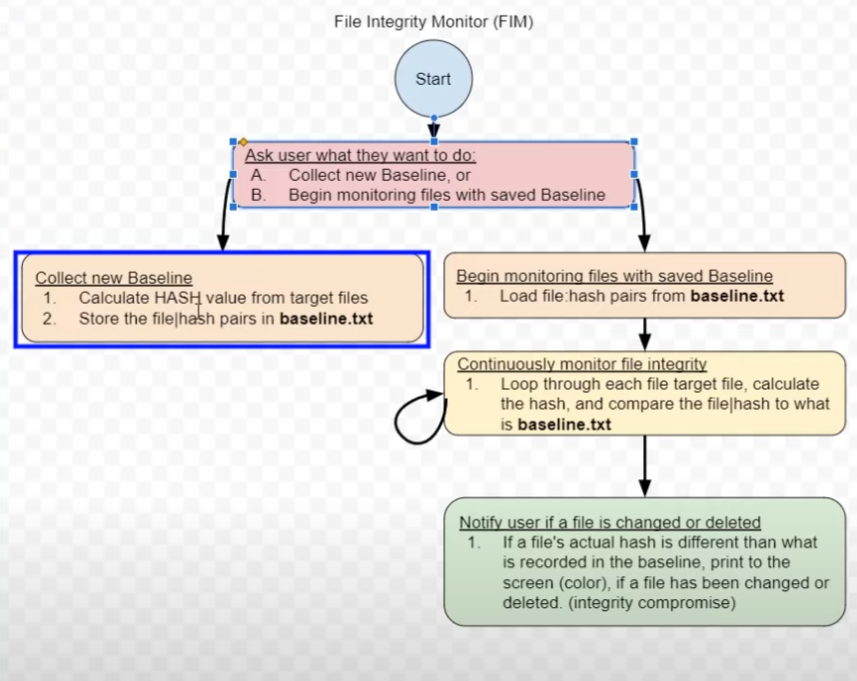 File Integrity Monitor Structure
File Integrity Monitor Structure
The first step is address what the user is aiming at accomplishing. They can either create a new baseline for a file which will calculate the hash of the target file(s) and store it in a text file.
Or, users can monitor a file that they already have a baseline. This will be done by loading the file hashes from the text file where it was saved previosuly in the baseline section. Then, the Powershell script will run continuously and loop through the target file hash(es), compare the result with the baseline and notify the user if anything has changed.
The language used for this script is powershell, it is the most versatile and has an awesome range of uses.
Show Me the Code
1
2
3
4
Function Calculate-File-Hash($filepath) {
$filehash = Get-FileHash -Path $filepath -Algorithm SHA256
return $filehash
}
The first function calculates the hash of the file with the $filepath parameter as the path, the SHA256 algorithm will be used. If this was more advanced a stronger algorithm would be used with salting the hash.
1
2
3
4
5
6
7
8
Function Erase-Baseline-If-Already-Exists() {
$baselineExists = Test-Path -Path .\baseline.txt
if ($baselineExists) {
# Delete it
Remove-Item -Path .\baseline.txt
}
}
Next is more so a utility function that will delete a file as a baseline if it already exists. You cant monitor what you are not measuring.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
if ($response -eq "A".ToUpper()) {
# Delete baseline.txt if it already exists
Erase-Baseline-If-Already-Exists
# Calculate Hash from the target files and store in baseline.txt
# Collect all files in the target folder
$files = Get-ChildItem -Path .\Files
# For each file, calculate the hash, and write to baseline.txt
foreach ($f in $files) {
$hash = Calculate-File-Hash $f.FullName
"$($hash.Path)|$($hash.Hash)" | Out-File -FilePath .\baseline.txt -Append
}
}
Moving on, the code above is executed if the user answers the letter a or A because of the .ToUpper() function. Here a hash will be calculated of all the files in the “./Files” directory and will be reported to the baseline text file.
Creating the baseline was more difficult than monitoring it…
1
2
3
4
5
6
7
8
9
10
elseif ($response -eq "B".ToUpper()) {
$fileHashDictionary = @{}
# Load file|hash from baseline.txt and store them in a dictionary
$filePathsAndHashes = Get-Content -Path .\baseline.txt
foreach ($f in $filePathsAndHashes) {
$fileHashDictionary.add($f.Split("|")[0],$f.Split("|")[1])
}
To start off, this code will create a dictionary for the file hashes and read in the content of the baseline via the Get-Content function. The foreach block will split each line of the baseline into key/value pair being [FilePath]|[Hash].
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
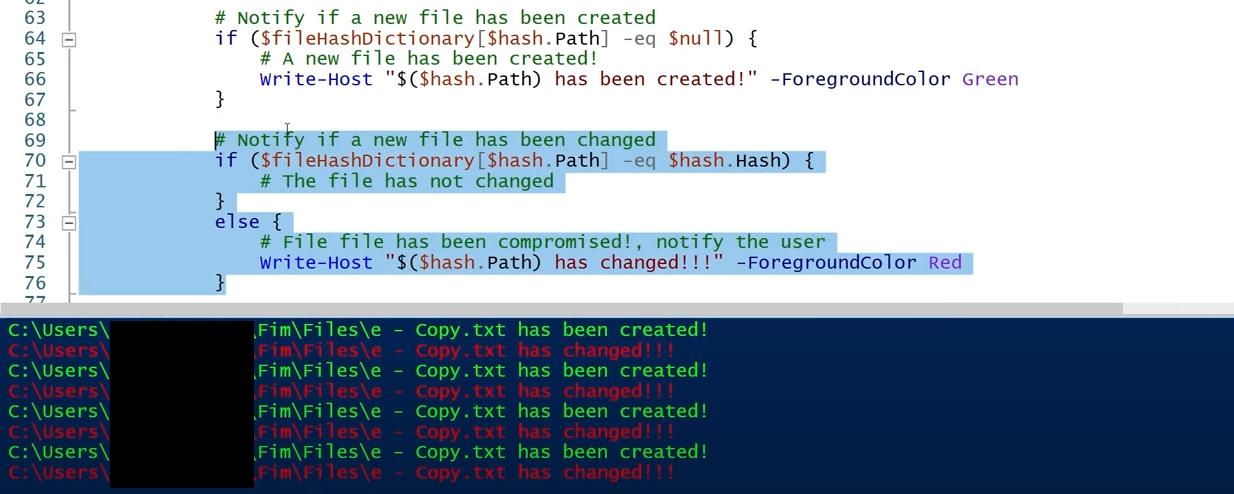
while ($true) {
Start-Sleep -Seconds 1
$files = Get-ChildItem -Path .\Files
# For each file, calculate the hash, and write to baseline.txt
foreach ($f in $files) {
$hash = Calculate-File-Hash $f.FullName
#"$($hash.Path)|$($hash.Hash)" | Out-File -FilePath .\baseline.txt -Append
# Notify if a new file has been created
if ($fileHashDictionary[$hash.Path] -eq $null) {
# A new file has been created!
Write-Host "$($hash.Path) has been created!" -ForegroundColor Green
}
else {
# Notify if a new file has been changed
if ($fileHashDictionary[$hash.Path] -eq $hash.Hash) {
# The file has not changed
}
else {
# File file has been compromised!, notify the user
Write-Host "$($hash.Path) has changed!!!" -ForegroundColor Yellow
}
}
}
Almost there… This next code part of the previous function will continuously monitor the file with the saved baseline. If a file has been changed or created the user will be notified and the color of the powershell editor will change.
All in All
In conclusion, implementing a robust file integrity monitoring (FIM) system is essential for strengthening cybersecurity defenses and upholding the integrity component of the CIA triad. FIM acts as a critical safeguard against unauthorized modifications or tampering with crucial files and data within an organization’s network.
By continuously monitoring and verifying file integrity, organizations can swiftly detect and respond to potential security breaches or malicious activities, thereby preserving data trustworthiness and reliability. Furthermore, FIM plays a significant role in helping organizations maintain compliance with regulatory standards and industry best practices, ensuring data integrity remains a cornerstone of cybersecurity strategies. As cyber threats continue to evolve, investing in FIM not only enhances security posture but also reinforces the resilience of organizational infrastructures against emerging threats, ultimately safeguarding the confidentiality, integrity, and availability of sensitive information.